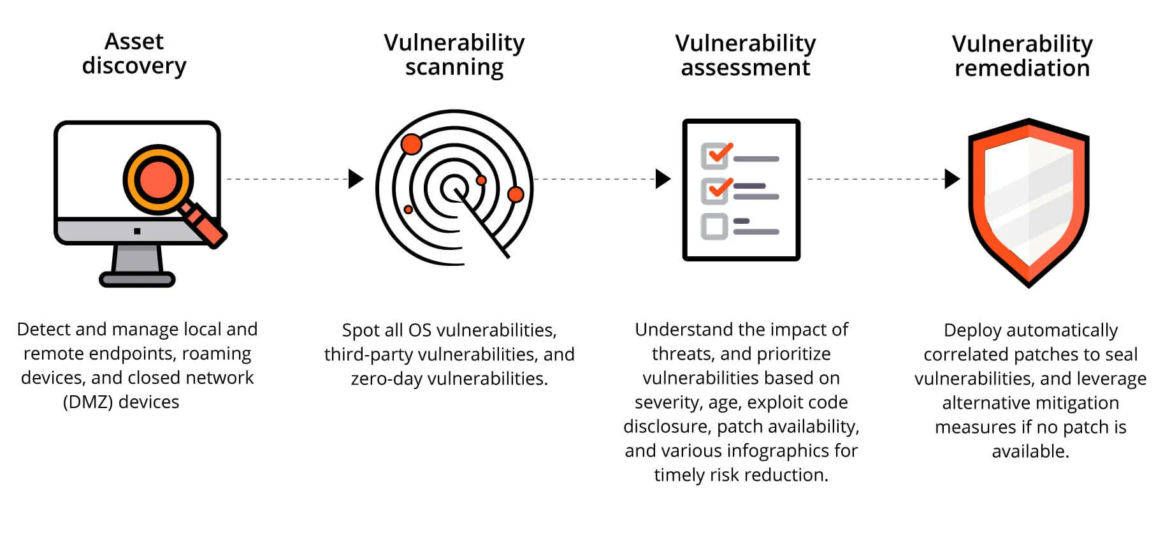
Vulnerability Assessments
At Agajservices, we offer comprehensive vulnerability assessment services designed to identify, evaluate, and prioritize security weaknesses within your organization’s systems, applications, and networks. Our assessments provide you with the critical insights needed to enhance your security posture and protect against potential threats.
Key Features:
Comprehensive Scanning: We utilize advanced scanning tools and techniques to assess your environment for vulnerabilities. This includes both automated and manual assessments to ensure thorough coverage.
Prescription:
- Automated scanning of network devices, servers, and applications
- Manual testing for complex and critical systems
- Identification of known vulnerabilities, misconfigurations, and security weaknesses
Risk Evaluation: After identifying vulnerabilities, we evaluate their potential impact on your organization. Our team provides a risk assessment that prioritizes vulnerabilities based on severity and likelihood of exploitation.
Prescription:
- Categorization of vulnerabilities based on CVSS (Common Vulnerability Scoring System) scores
- Risk analysis to determine potential business impacts
- Prioritization of vulnerabilities for remediation efforts
Reporting and Recommendations: We provide detailed reports that outline the findings of the vulnerability assessment, including actionable recommendations for remediation. Our reports are tailored to your audience, from technical teams to executive leadership.
Prescription:
- Comprehensive assessment reports detailing identified vulnerabilities
- Actionable remediation steps and best practices
- Executive summary for high-level stakeholders
Remediation Support: Our team offers support in addressing identified vulnerabilities. We work closely with your IT staff to implement recommended fixes and enhancements to your security infrastructure.
Prescription:
- Assistance with patch management and updates
- Configuration changes to improve security
- Validation of remediation efforts to ensure effectiveness
Continuous Monitoring: Cyber threats are constantly evolving, which is why we offer ongoing vulnerability monitoring and assessments. This proactive approach helps you stay ahead of potential risks.
Prescription:
- Regular vulnerability scans to identify new weaknesses
- Continuous improvement of security measures based on findings
- Alerts and notifications for newly discovered vulnerabilities
Compliance Support: Many regulations require regular vulnerability assessments as part of their compliance requirements. We help you meet these requirements while enhancing your overall security posture.
Prescription:
- Assistance with compliance assessments (e.g., PCI DSS, HIPAA)
- Documentation and reporting for compliance audits
- Recommendations for achieving and maintaining compliance
